Webmasters should be jealous of their own web site; regardless it is a little one or a huge site.
After all, all the time spent on designing and creating the template, than in creating valuable asset for the users, cannot really be estimated in monetary figures if this is not a business site with a project, a deadline and a budget already in place.
And guess what? It is horrible to discover that the site where you invested an incredible amount of hours is not even indexed on the search engine because it seeds malware or serving a cloaked version of your pages.
Hackers can use deceitful techniques to mask their shady tentative to make money using your site. This can take out in many forms like:
- Hidden text (very old fashioned) but still common;
- A cloaked version of your page; you see your site, search engines something different;
- Embedded code from third party sites;
- Inclusions of malware or script to render unexpected things;
- Redirect to other sites, either random or the same one;
- Perform actions on a specific moment of the day
So what should you do to diagnose your hacked site?
RULE NUMBER ONE: Do not open your site!
Chances are that a compromised site has been quickly identified as such and an online service has already classified it thus making your browser showing one of those intimidating warnings that should let ring a bell on top of your head.
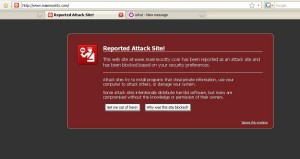
By keep going and connecting to your site you will help the malware proliferate on the net as you suddenly become a healthy carrier.
RULE NUMBER TWO: Investigate with a pool of online tools
There are many sites that can help you discover whether a site has been compromised and what sort of damage they got.
For instance, I do often run parallel checks using both sucuri.net as well as the Google Safe Browsing service.
Both the above don’t require you to have an account with the specified service.
If those tools are not revealing anything, in this circumstance you have to move next.
The best alternative is to have a look at your webmaster tools, either Google or Bing. Both of these are normally sending you an email if your site is verified and you have configured them to send you over relevant emails as soon as circumstances change (so it’s not just about malware and spam).
For instance the “Fetch the page as Google” is useful to see what Google sees when it crawls the page; querying the cache of search engines (assuming you haven’t block it at all) it may work as well.
RULE NUMBER THREE: Investigate with a pool of offline tools
Perhaps offline it’s not the best word ever in this circumstance, as you still need to be connected to Internet, unless you have dumped your site for checking it with an Antivirus (assuming the one you will be using is able to check for specific coding patterns).
So I will limit my “offline” verification to just a couple of tests that can be performed with a command called cURL (natively available in *nix system, and available to download for Windows).
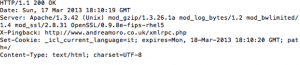
The first method is to check the headers of your site (or page) by typing the following:
cURL –I http://www.mysite.org
This will allow seeing the server response and checking whether something has changed on your .htaccess file; for instance there could be a hidden redirect.
 The second test is to dump a specific file to your hard disk, to further investigate into the source code. Once again, do not open in your browser, because it would be almost the same of running the code on your site.
The second test is to dump a specific file to your hard disk, to further investigate into the source code. Once again, do not open in your browser, because it would be almost the same of running the code on your site.
In order to perform this operation, the command to use is cURL –O URL
where you have to replace URL with the full URI you want to download whilst ensuring the o to be UPPERCASE, unless you want to rename the file in which case the lowercase version will be fine.
I hope you have found this article useful for your web site maintenance and I look forward to reading your commentaries.

